What is NAT?
I'll start with the basics. NAT stands for network address translation. It translates the real IP address of a device to the mapped IP and vice versa.
Real IP: the actual IP address of the device generating the traffic (on the inside interface in the examples below)
Mapped IP: the IP address the ASA translates the real IP address to (on the outside interface in the examples below).
NAT is most often used to translate private RFC 1918 IP addresses to publicly routable IP addresses (there are other less common uses as well).
For example:
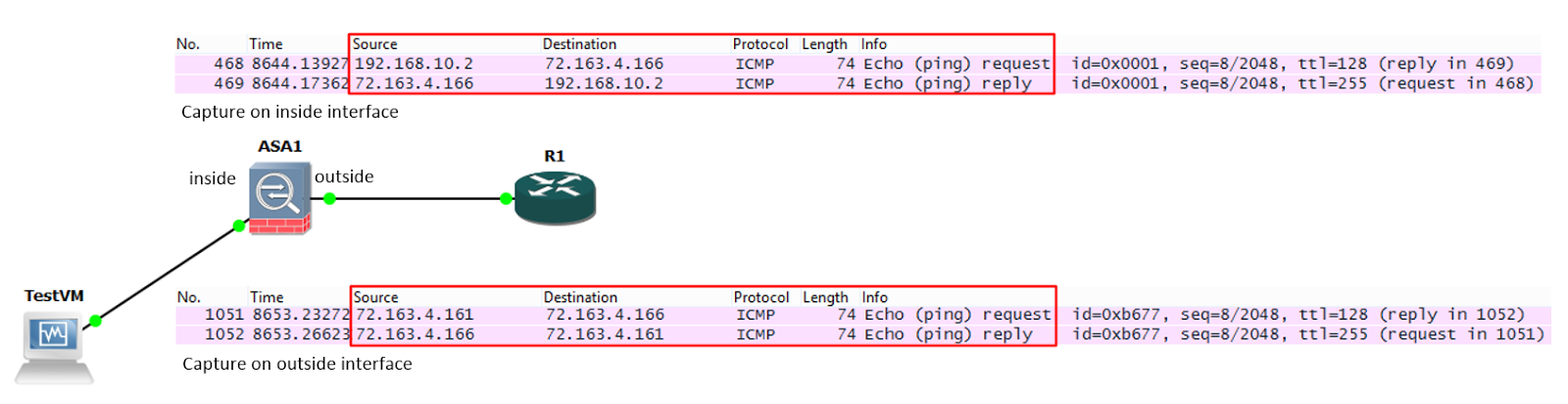
A ping is sent from TestVM (192.168.10.2) to R1 (72.163.4.166). In this example, R1 is on the internet, so the ASA cannot route the private address of 192.168.10.2 to R1. It must NAT the packet.
We can see this happen in the Wireshark captures below: